cybersecurity solutions
Extended detection and response (XDR) benefits and limitations
Extended detection and response (XDR) is a holistic cybersecurity solution that provides critical visibility into threats targeting endpoints, networks, and cloud services.
XDR solutions are often regarded as a necessary upgrade from endpoint-focused solutions like EDR, however, XDR is not without it's drawbacks and limitations.
Understanding the benefits and limitations of XDR is important in choosing the right cybersecurity solution for your business.
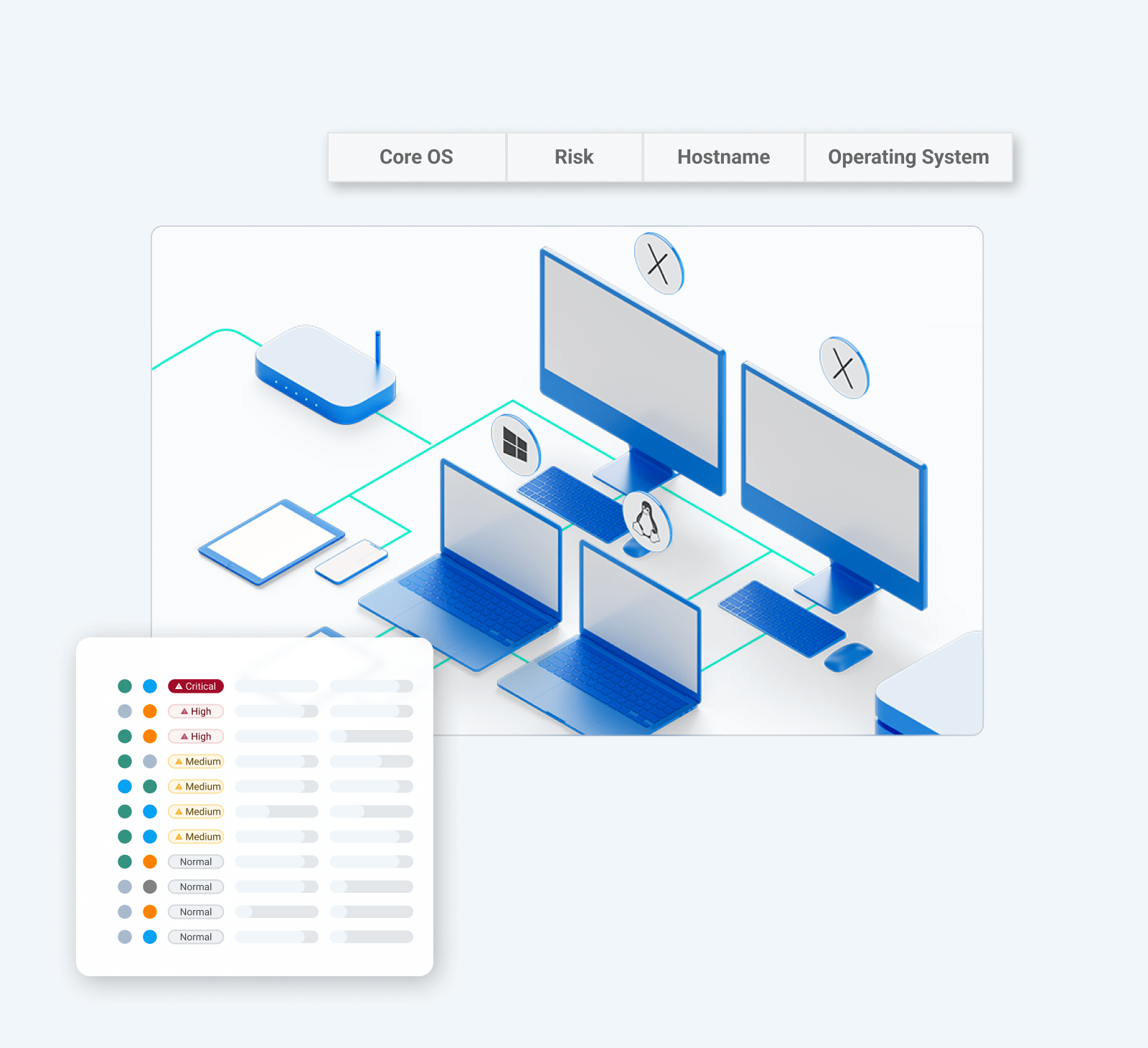
XDR solution strengths and challenges
What is extended detection and response (XDR)?
Extended detection and response (XDR) is a unified security solution that integrates data across multiple security layers, often including endpoints, networks, cloud workloads, and more.
XDR solutions attempt to provide a more comprehensive and cohesive approach to threat detection, analysis, and response by breaking down traditional security silos and offering visibility across an organization's entire IT environment.
In today’s world of hybrid work environments, complex IT infrastructures, and increasingly sophisticated threats, XDR solutions strive to deliver relevant information and threat data. This helps organizations better protect their data and operations, providing a more holistic approach to cybersecurity.
XDR strengths and benefits
XDR solutions recognize that indicators of compromise don't appear only at endpoints. The holistic nature of XDR offers these key benefits:
- Improved detection and response: By focusing on the entire threat landscape, XDR helps businesses identify and address threats targeting any part of their IT infrastructure.
- Centralized user interface: A key advantage of XDR is its ability to consolidate all threat data into a single dashboard, making it easier for teams to prioritize their responses.
- Lower total cost of ownership: By streamlining security toolsets, XDR solutions often help organizations find efficiencies and maximize their resources.
Extended detection and response solutions provide a wider array of coverage than basic solutions, and are presented in a unified package. This balance of simplified complexity makes XDR a strong choice for business threat protection.
XDR challenges and limitations
XDR takes its broad approach to cyber threat monitoring by pulling together multiple pieces of technology to deliver greater insight into an IT environment—but even this approach has its drawbacks:
- Not truly unified: XDR solutions are often constructed from various components that weren't developed cohesively, leading to integration issues. Each part of the platform might only offer a partial view of the overall picture.
- Excessive noise: XDR solutions can generate a significant number of alerts. Without proper tuning, the volume of false positives can overwhelm security teams, making it harder to identify real threats.
- Hard to manage: Managing XDR requires a high level of expertise in threat detection, response, and security operations. Many organizations struggle to find personnel with the necessary skills to operate these solutions effectively.
In principle, XDR unifies many technologies. But the current state of XDR solutions is not true unification. Rather, XDR is often a bundle of individual solutions feeding into a single dashboard. This leaves potential threat detection gaps in some areas and confusion in others.
What is endpoint detection and response (EDR)?
Endpoint detection and response (EDR) focuses on securing endpoint devices—any device with connections to and from a network. Endpoints typically include laptop and desktop computers, smartphones, tablets, Internet-of-Things (IoT) devices, servers, and more.
Where modern EDR truly sets itself apart is with a greater focus on active monitoring and the ability to identify abnormal or suspicious activity—which may go beyond known threats—and react appropriately. For example, actions taken could include active blocking, isolating a host, or escalating findings for further investigation. This is a stark contrast to classification-based detection because it adds a layer of intelligence to the system; classification-based detection requires previous experience or understanding of threats.
EDR strengths and benefits
EDR tools play a significant role in proper cybersecurity. They offer these three major strengths and benefits to businesses:
- Improved protection vs. antivirus software
- Cover endpoints well, which are a considerable portion of an organization's threat surface.
- Continuous monitoring of endpoints allows for rapid threat detection and response.
Endpoint security is a significant step up from antivirus software alone. EDR tools offer a broader coverage of endpoint threat detection. Combined with ongoing monitoring and rapid response, EDR provides a strong cybersecurity base for most businesses.
EDR challenges and limitations
While EDR is stronger than traditional antivirus protection, it also has some major weak points. Here are a few key reasons why EDR alone can't fully protect modern organizations from advanced cyberattacks:
- EDR is a reactive, not proactive, approach to cybersecurity. EDR simply responds to threats, it does not prevent them.
- Endpoint-only protection leaves significant security gaps, exposing vulnerabilities.
- EDR requires deep expertise to properly manage. Without it, EDR can be highly ineffective.
Relying solely on EDR leaves exploitable gaps in network visibility and protection.
XDR vs managed detection and response (MDR)
Managed detection and response (MDR) is an outsourced security service in which a team of third-party experts handles threat monitoring, detection, and response capabilities. MDR service providers use a strategic mix of human intelligence and sophisticated technologies to provide superior threat detection and response for businesses.
| Extended detection and response (XDR) | Managed detection and response (MDR) | |
| Capabilities |
|
|
| Coverage |
|
|
| Benefits |
|
|
| Limitations |
|
|
FIND THE RIGHT CYBERSECURITY SOLUTION
Free guide: Optimizing your cybersecurity stack
Having the wrong or too many security tools in your stack is tedious, time-consuming, and costly—and could even put your business at risk.
Learn how to optimize your security stack so you have the best cybersecurity solution available while putting hours back in your day and money back in the budget.
XDR vs MDR: What's right for you?
Important points to consider
Choosing the right cybersecurity solution for your business is critical, but doesn't need to be complicated. Start by asking these important questions:
- Do we have the expertise and resources to manage an XDR?
XDR requires deep expertise to manage properly. The extended coverage is a significant step forward in proper cybersecurity, but the volume and complexity of alerts can be hard to handle. Without proper management, a business does not have proper defense against serious threats.
MDR alleviates a large burden on your in-house security team (if you have one) and ensures your tools are managed properly. - What could a cyberattack cost us?
Cybersecurity threats continue to evolve, using new techniques and exploits to gain access to important business information. Threat actors can then hold that data for ransom, or openly share the information and damage the victim's reputation. Investing in holistic, properly managed cybersecurity that proactively prevents threats is worth the investment.
Choosing the right MDR solution
MDR solutions are often considered the best option for a company's cybersecurity. There are many MDR service providers, and it's vital you make an informed choice when choosing your partner.
- Not all MDR services provide complete threat protection.
MDR service offerings vary widely. Some will just offer to manage an endpoint detection and response (EDR) solution for you, which won't offer the comprehensive coverage businesses need today. Other MDR providers encompass a more holistic approach that protects endpoints, cloud services, networks, and more.
- Some MDR solutions use disparate tooling.
Some MDR services are merely several disparate tools under one umbrella solution. This approach requires managing multiple tools, adding unnecessary complexity, and can even expose your business to threats. Prioritize MDR solutions with natively built, holistic approaches. - The best MDR prioritizes supporting your business.
Your MDR provider should be your partner, but not all MDR services see it that way. A great MDR provides simple, accessible information and expert recommendations and support whenever you need it.
compare leading mdr vendors
Report: MDR Emotional Footprint 2024
SoftwareReviews, a division of Info-Tech Research Group, had users rate MDR vendors in 25 categories, including service experience, strategy & innovation, and product impact.
Why customers choose Field Effect MDR
Made for SMBs
People, process, and technology
Risk management
Hands-free cybersecurity
HEAR FROM FIELD EFFECT MDR USERS
Field Effect MDR: Buyer Experience Report
Read this Buyer Experience Report to learn what real Field Effect MDR users have to say about the product and why it "is a clear leader in terms of value and features for SMBs."
CyberSecurity is our Priority
About Field Effect
Field Effect, a global cybersecurity company, is revolutionizing the industry by bringing advanced cybersecurity solutions and services to businesses of all sizes. We build solutions that are sophisticated, yet easy to use and manage, so every business owner can get the hands-free cybersecurity they expect and the sleep-filled nights they deserve.
Field Effect
Cybersecurity made simple.
Businesses of all sizes should have access to world-class cybersecurity.


