cybersecurity solutions
Choosing the right MDR solution.
Choosing the right managed detection and response provider can feel like a big decision, especially with so many options available. The truth is, not all MDR providers are created equal—what works for one business might not be the best fit for yours.
But it doesn’t have to be overwhelming. We’re here to make it simple.
Below, we break down key differences between MDR providers and highlight how factors like your business size, structure, and unique cybersecurity needs should shape your decision.
3 key considerations when choosing an MDR solution.
Breadth of coverage
In cybersecurity, breadth of protection is everything. It’s about ensuring every part of your business is actively monitored and safeguarded against threats. Partial protection isn’t enough, and not all managed detection and response services deliver the same level of comprehensive defense.
To truly secure your business, your MDR provider should offer seamless, end-to-end protection across:
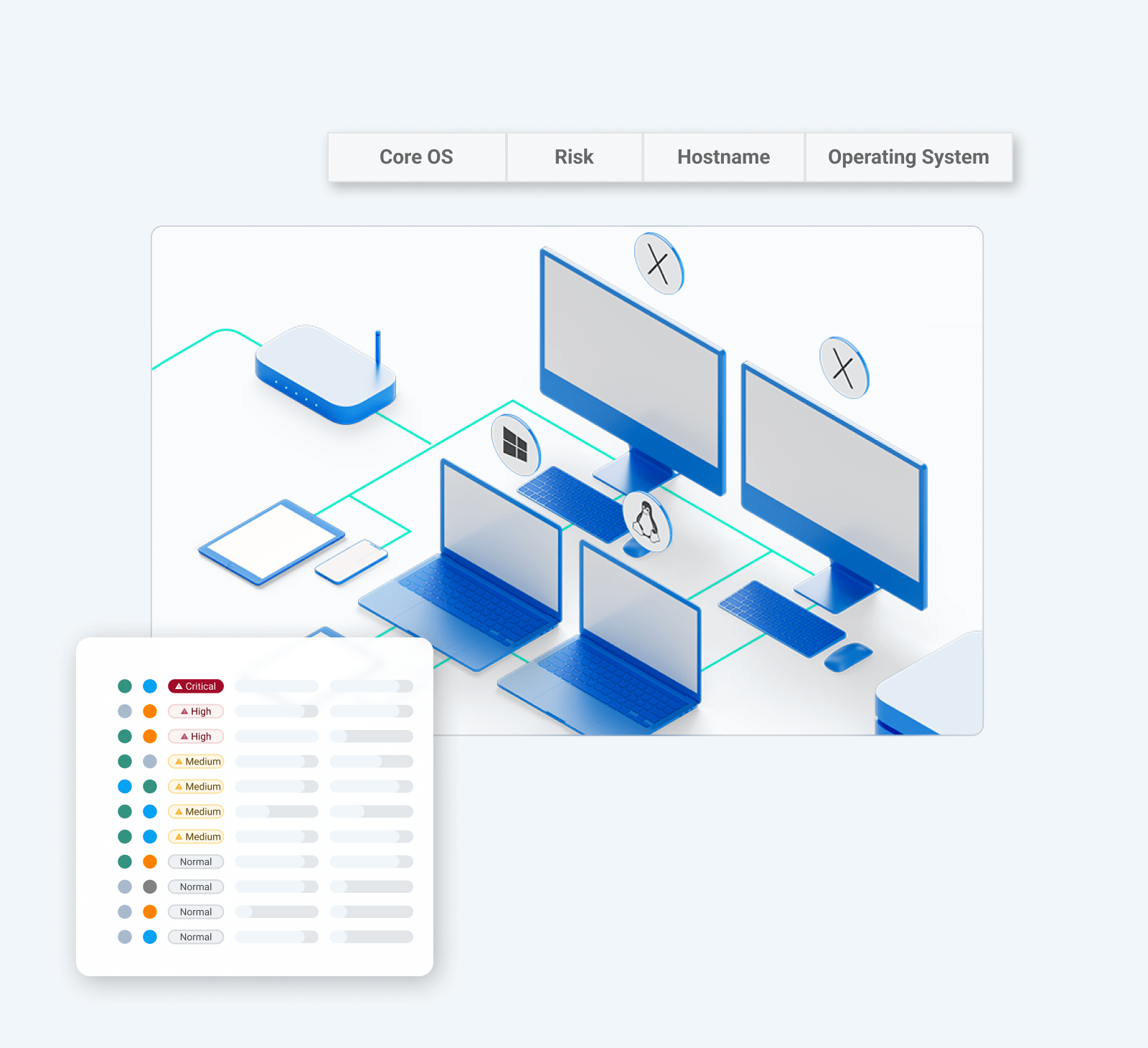
- Endpoints: Devices like laptops, mobile phones, and servers that connect to your network.
- Cloud: The critical data, applications, and infrastructure your business relies on in the cloud.
- Network: Users, web traffic, and the protocols that govern your network's communication.
Be aware that some MDR providers piece together solutions from multiple platforms, which can leave small but significant gaps in protection and lead to unnecessary duplicative alerts. The most effective providers use purpose-built, integrated solutions that deliver seamless coverage across all these areas—eliminating vulnerabilities and ensuring your business is fully protected.
Simplicity of use
A truly comprehensive managed detection and response system is built on a foundation of advanced tools and technologies. But, the best MDR providers deliver this sophistication with simplicity—keeping the complexity behind the scenes while offering an intuitive, user-friendly experience.
Simplicity doesn’t mean fewer features; it means making powerful capabilities accessible and easy to use for everyone involved. For example, the right MDR provider ensures that alerts are:
- Noise-free: Intelligently consolidating alerts to avoid duplicates and show only the most relevant threats.
- Prioritized: Categorizing alerts based on risk level and severity makes it easy to know where to invest your time first.
- Actionable: Delivering clear, actionable alerts with straightforward instructions to resolve the issue, not just a notification that the issue exists.
The best MDR providers strike a balance of robust, feature-rich protection with a simple, intuitive platform.
Partners vs vendors
MDR providers vary widely in what they offer. Some operate as basic software vendors, providing setup and pay-as-you-go support. Others go beyond the basics, acting as an extension of your team and delivering hands-on, expert guidance.
When evaluating vendors, short-list those who offer:
- 24/7 monitoring, response, and support. Cyberattacks don't follow a 9-5. Around-the-clock monitoring and expert response are essential for continuous protection.
- Deep expertise. No two businesses or networks are alike. Look for providers with highly skilled experts who can identify emerging risks, analyze suspicious activity, and keep your organization secure.
- Empower your team. Even with a strong internal IT or cybersecurity team, an MDR provider with a fully staffed Security Operations Center (SOC) can extend your team’s capacity and capabilities. They handle the heavy lifting—monitoring, threat hunting, and response—so your team can focus on strategic priorities.
The best MDR providers don’t just offer protection—they serve as trusted partners, combining deep expertise with comprehensive services. They give you the benefits of an in-house cybersecurity team at a fraction of the cost.
What is endpoint detection and response (EDR)?
Endpoint detection and response (EDR) focuses on securing endpoint devices—any device with connections to and from a network. Endpoints typically include laptop and desktop computers, smartphones, tablets, Internet-of-Things (IoT) devices, servers, and more.
Where modern EDR truly sets itself apart is with a greater focus on active monitoring and the ability to identify abnormal or suspicious activity—which may go beyond known threats—and react appropriately. For example, actions taken could include active blocking, isolating a host, or escalating findings for further investigation. This is a stark contrast to classification-based detection because it adds a layer of intelligence to the system; classification-based detection requires previous experience or understanding of threats.
EDR strengths and benefits
EDR tools play a significant role in proper cybersecurity. They offer these three major strengths and benefits to businesses:
- Improved protection vs. antivirus software
- Cover endpoints well, which are a considerable portion of an organization's threat surface.
- Continuous monitoring of endpoints allows for rapid threat detection and response.
Endpoint security is a significant step up from antivirus software alone. EDR tools offer a broader coverage of endpoint threat detection. Combined with ongoing monitoring and rapid response, EDR provides a strong cybersecurity base for most businesses.
EDR challenges and limitations
While EDR is stronger than traditional antivirus protection, it also has some major weak points. Here are a few key reasons why EDR alone can't fully protect modern organizations from advanced cyberattacks:
- EDR is a reactive, not proactive, approach to cybersecurity. EDR simply responds to threats, it does not prevent them.
- Endpoint-only protection leaves significant security gaps, exposing vulnerabilities.
- EDR requires deep expertise to properly manage. Without it, EDR can be highly ineffective.
Relying solely on EDR leaves exploitable gaps in network visibility and protection.
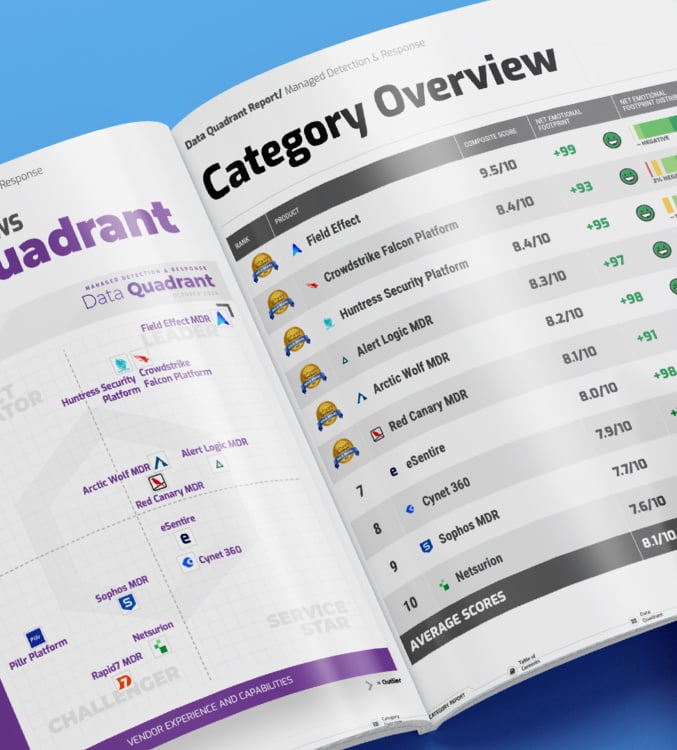
COMPARE LEADING MDR VENDORS
MDR Data Quadrant Report
The Latest Data Quadrant Report analyzes over 300 reviews across 16 MDR vendors, including Field Effect.
This third-party report is designed to help organizations like yours make informed decisions, drawing on the experiences of those who use these products daily. See how over 300 active MDR users rank the top MDR service providers, including:
- Field Effect
- Crowdstrike
- Huntress
- Sophos
- Arctic Wolf
Why customers choose Field Effect MDR
Made for SMBs
People, process, and technology
Risk management
Hands-free cybersecurity
Seamless Cybersecurity with Field Effect
The power of 15+ tools. The simplicity of one.
From prevention to threat detection and response, Field Effect MDR has you covered from end to end.
Higher alert fidelity
Field Effect MDR correlates data across the entire IT environment, removing the noise, false positives, and duplicate alerts that occur when using overlapping or limited cybersecurity tools. Field Effect alerts are context-rich and prioritized by severity. You are notified when it’s time to act and with precise guidance on how.
Greater value
Each additional cybersecurity tool may mean more upfront and long-term costs. Field Effect MDR is an all-in-one solution that delivers greater value compared with layering multiple tools with multiple payments.
Streamlined operations
Reduce or eliminate the need to deploy, configure, and manage multiple systems. Field Effect MDR displays all important threat data through a single dashboard. Stop spending time working between applications to analyze and correlate threat data.
Improved visibility
Field Effect MDR eliminates siloes, providing complete visibility into vulnerabilities and risks across your entire threat environment without having to manage multiple tools to fill gaps.
FIND THE RIGHT CYBERSECURITY SOLUTION
Free guide: Optimizing your cybersecurity stack
Having the wrong or too many security tools in your stack is tedious, time-consuming, and costly—and could even put your business at risk.
Learn how to optimize your security stack so you have the best cybersecurity solution available while putting hours back in your day and money back in the budget.
The standout feature is its continuous 24/7 monitoring of all network traffic, providing unparalleled vigilance.
It has taken the place of several cybersecurity solutions for us, including replacing a previous SOC vendor.
We now have a single cybersecurity product that protects all of our threat surfaces, and all the endpoints.
I'd recommend the product. I'd rate the solution ten out of ten.
But in the event that someone clicks on something they shouldn't, [Field Effect MDR] will isolate it and quarantine it.
HEAR FROM FIELD EFFECT MDR USERS
Field Effect MDR: Buyer Experience Report
Read this Buyer Experience Report to learn what real Field Effect MDR users have to say about the product and why it "is a clear leader in terms of value and features for SMBs."
CyberSecurity is our Priority
About Field Effect
Field Effect, a global cybersecurity company, is revolutionizing the industry by bringing advanced cybersecurity solutions and services to businesses of all sizes. We build solutions that are sophisticated, yet easy to use and manage, so every business owner can get the hands-free cybersecurity they expect and the sleep-filled nights they deserve.
Field Effect
Cybersecurity made simple.
Businesses of all sizes should have access to world-class cybersecurity.