EDR-XDR-MDR
What is the difference between MDR, XDR, and EDR and how to pick the right provider?
These three approaches are hot topics in the security sector and dominate a lot of conversation:
- MDR, which stands for managed detection and response.
- XDR, which stands for extended detection and response.
- EDR, which stands for endpoint detection and response.
Fill out the form to access a complimentary report to help you pick the right MDR provider.
MDR, XDR, and EDR at a glance
What is managed detection and response (MDR)?
As helpful as EDR and XDR can be for an organization, they’re not without challenges. Tools that simply compile activity data, whether from endpoints alone or other areas of your IT infrastructure, generate a wealth of data that requires further analysis. In turn, this increases workloads and requires an in-depth understanding of cybersecurity telemetry and processes. This is the challenge that managed detection and response seeks to address.
MDR is not a specific technology, but a managed service that packages the benefits of EDR and/or XDR into a convenient offering, helping offload some of the challenges of hiring cybersecurity professionals who have the experience needed to build an in-house security program.
What is extended detection and response (XDR)?
XDR’s origins come from the fact that looking through a single lens at an organization’s infrastructure simply doesn’t provide the coverage and visibility required to minimize the threat surface.
EDR and some traditional MDR offerings are frequently seen as limited point solutions, addressing a single aspect within a network. XDR is a direct response to those limitations, pulling together detection and response capabilities for endpoints, networks, and cloud services in a single platform. XDR is often offered as software-as-a-service (SaaS), making it easier for businesses to access this technology.
What is endpoint detection and response (EDR)?
Endpoint detection and response (EDR) focuses on securing endpoint devices—any device with connections to and from a network. Endpoints typically include laptop and desktop computers, smartphones, tablets, Internet-of-Things (IoT) devices, servers, and more.
Where modern EDR truly sets itself apart is with a greater focus on active monitoring and the ability to identify abnormal or suspicious activity—which may go beyond known threats—and react appropriately. For example, actions taken could include an active block, isolating a host, or escalating findings for further investigation. This is a stark contrast to classification-based detection because it adds a layer of intelligence to the system; classification-based detection requires previous experience or understanding of threats.
At a glance, MDR, XDR and EDR
| MDR | XDR | EDR | |
| Capabilities |
|
|
|
| Coverage |
|
|
|
| Benefits |
|
|
|
| Limitations |
|
|
|
While closely related, there are several major differences—not to mention subtler nuances—that differentiate these approaches to security from one another. Without a clearer understanding of the actual outcomes each one provides, businesses may struggle to make an informed decision about the solution(s) they need to defend their operations and data.
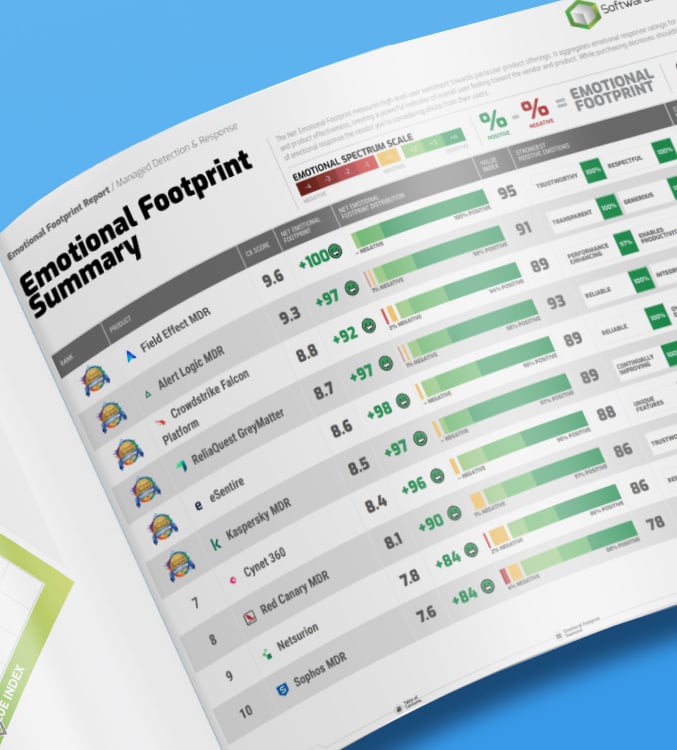
THIRD-PARTY REPORT
Field Effect Covalence: Buyer Experience Report
Read this Buyer Experience Report to learn what real Field Effect Covalence users have to say about our product and why "Covalence is a clear leader in terms of value and features for SMBs."
CyberSecurity is our Priority
About Field Effect
Field Effect, a global cybersecurity company, is revolutionizing the industry by bringing advanced cybersecurity solutions and services to businesses of all sizes. We build solutions that are sophisticated, yet easy to use and manage, so every business owner can get the hands-free cybersecurity they expect and the sleep-filled nights they deserve.
Field Effect
Cybersecurity made simple.
Businesses of all sizes should have access to world-class cybersecurity.